Bulk User Creation Plugin in IdentityIQ
Introduction
A plugin is a tiny piece of software that extends the functionality of an Application or Computer program.
The IdentityIq Plugin Framework is an protract framework model for IdentityIQ.It allows third parties to develop affluent application and service-level amplification to the core SailPoint IdentityIQ. It enables plugins to extend the excellence in user interface, deliver custom REST endpoints, and to deliver conventional background services.
In the following presentation, I will be providing a brief introduction of IdentityIQ Plugins:
Plugin Versioning Requirements
Plugin version numbers must be numeric, denote the parts of the version number with decimal points, and not contain any alphabetic or other characters in order to better facilitate upgrading plugins.
Leading zeroes will be removed from each segment of the version number, and the values between the decimal points are converted to integers.
For example:
06 and 00006 are both interpreted as 6
A segment containing any non-numeric values is interpreted as 0
7.009.alpha is parsed as 7.9.0
5.7.8a is parsed as 5.7.0
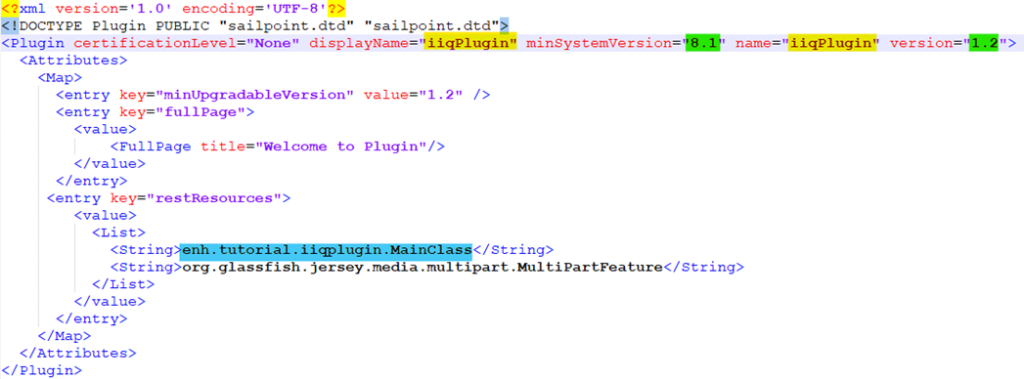
Plugin Object Model
The Plugin XML object, which specifies the plugin’s constant, describes a plugin in IdentityIQ. REST resources, Snippets, and settings are a few examples of features. The manifest.xml file contains the definition of the Plugin object. This file is necessary for plugin.
The XML object known as the Plugin Object defines the plugin’s feature. By binding them as attributes of a Plugin Object, this object informs IdentityIQ about the facets that are present in your plugin. You can also specify information about the plugin in the Plugin Object, such its name, the privileges needed to use it, its version, snippets, and REST resources. Use the advanced plugin settings to define a form or to refer to a specific plugin configuration file for more complicated plugins that need support for several field types and more dynamic behavior, such as drop-down lists or password fields. Depending on past selections, dynamic behavior can involve showing or hiding other fields.
For Example: In contrast to when the user picks basic authentication, it could be more acceptable to display an access token field when the user selects o-auth authentication.
Plugin Settings
Attributes that can be changed during installation are known as plugin settings. To view the configuration options page, click Configure. Forms are used to display the settings. The form is generated automatically if the plugin does not use its advanced options.
On the plugin settings page, the settings from the manifest file are shown in alphabetical order.
A single setting on a plugin’s configuration settings page can be represented by the Plugin setting object. On the settings page, each object serves to represent a single customizable setting.
Developing Plugins
IdentityIQ stores the .zip archive file of the Plugin in the IdentityIQ database in the spt_file_bucket table. The data in the spt_file_bucket table is a referenced ID to an entry in the spt_persisted_file table.
After establishment or amid an application server restart, plugins are stacked from this.zip file. All consequence files are taken from the.zip file and cached for ensuing utilization. The cached files can be gotten to using a assortment of accessor ways, but they can moreover be retrieved by utilizing
the URL prefix /identityiq/plugin/pluginName taken after by the way indicated within the construct structure. The PluginClassLoader lesson is utilized to stack and cache compiled Java classes from the.zip file.
Example Plugin Directory Structure:
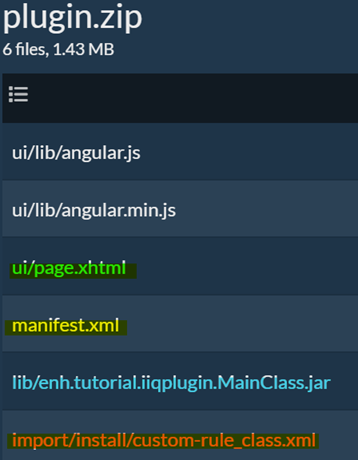
Bulk User Creation Plugin
This is a custom plugin built by ENH iSecure for creating Identities through SailPoint IdentityIQ and Provision the following identities to the requested Applications in IdentityIQ
A User like a manger level will have a Privilege to request for Bulk User Creation, once a .csv file is Uploaded in UI page by the following user and if the users request gets Approved a bulk number of identities will be created in Sailpoint IdentityIQ and the following identities provisioning takes place on the identities joining dates for the Requested Applications and following Email notification follows with respective action steps.
In the following video, I will be providing a detailed demo on IdentityIQ custom Plugin (Bulk User Creation)