
Mis-utilization of access controls in any system has been an age old problem. Such mis-utilizations lead to serious scandals similar to Enron and MF Global in USA and Satyam scandal in India. Also they would lead to serious internal losses in the organization which could have been prevented with an identity management solution in place.
The exploitation in access controls have grown to great extents that heavily stringent laws to be followed by every organization like SoX and HIPAA have been enforced. The prime objectives of these laws is to strictly assess access control in an organization to ensure that best practices are followed to make sure access control is not misutilized.
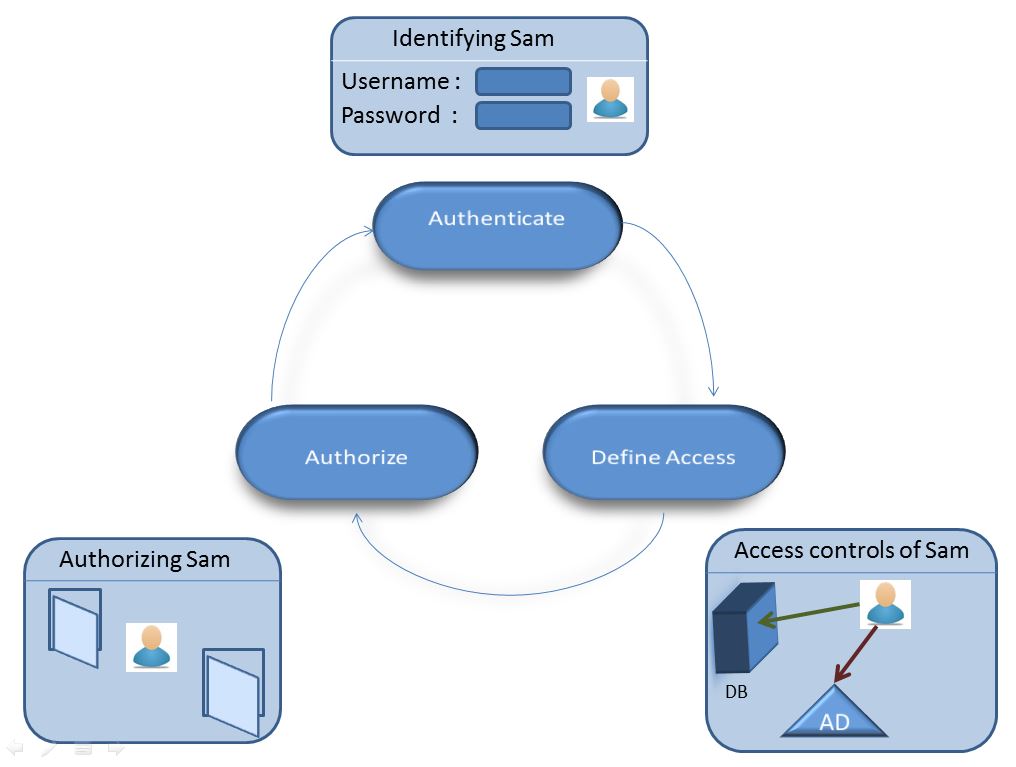 Identity management is the domain which would help the organizations solve most of the problems related to access control that could be solved by proper authentication, authorization and accountability.
Identity management is the domain which would help the organizations solve most of the problems related to access control that could be solved by proper authentication, authorization and accountability.
Identity management solves these problems by strictly monitoring the life-cycle of an enterprise identity. Identity management solutions automate the processes of joiner, mover, leaver (which are the various phases of life-cycle of digital identity).
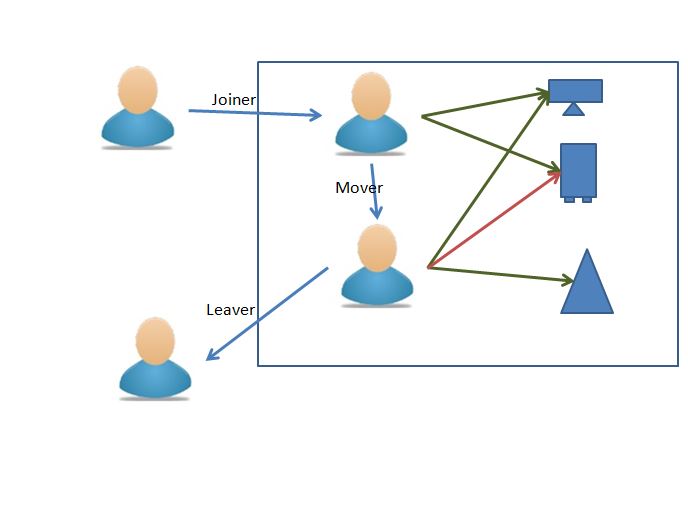 To monitor the JML process , identity management solutions follow various mechanisms through which CIA is actually achieved. The following are the mechanisms that are followed :
To monitor the JML process , identity management solutions follow various mechanisms through which CIA is actually achieved. The following are the mechanisms that are followed :
Maintaining and updating the identity repository :
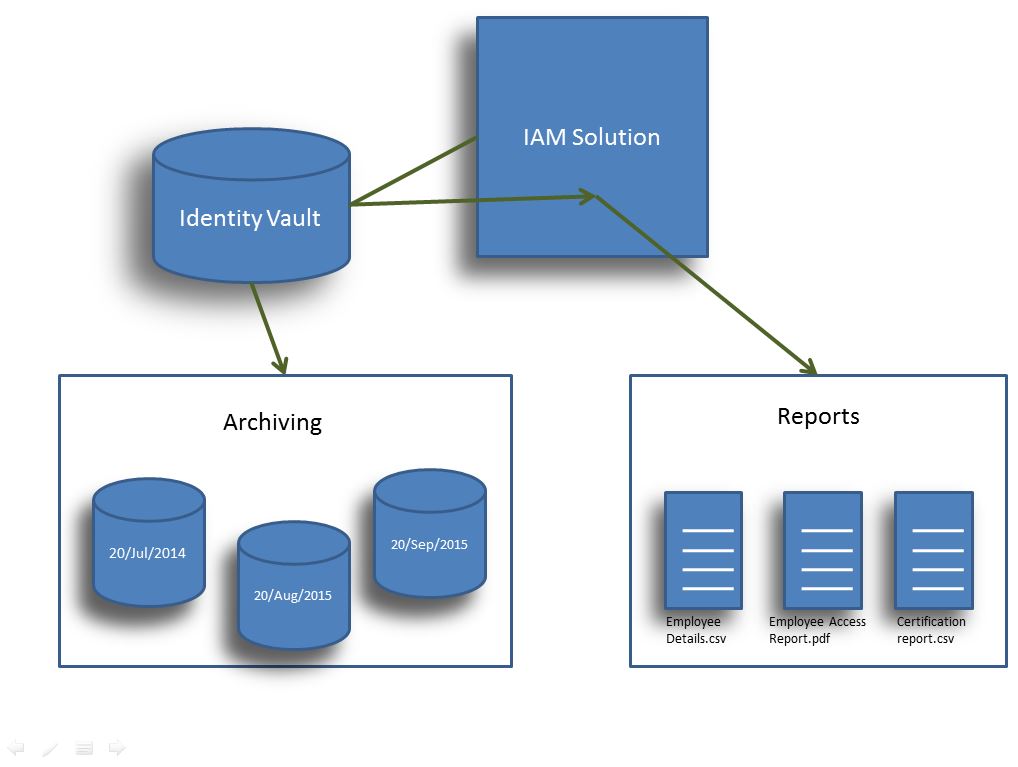
An identity repository or identity vault is a huge collection of all the digital identities and a mapping of various access controls to each digital identity. It serves as base to any identity management operations.
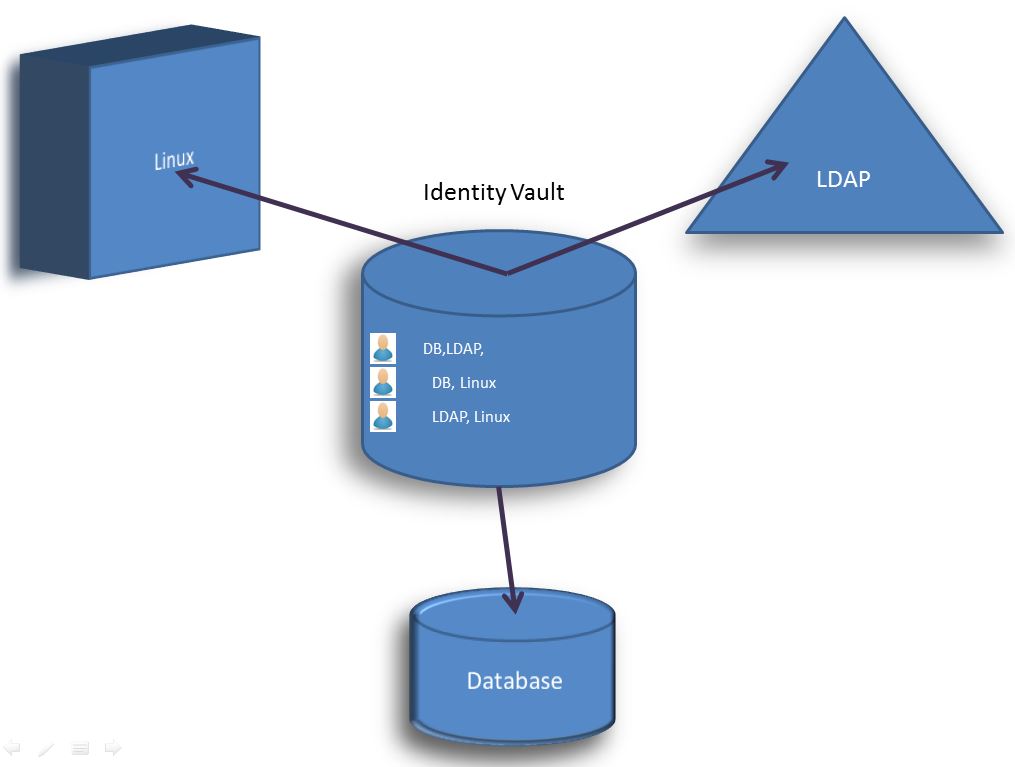
Identity repository is created as a very first step of any identity management solution. This simply means that we have track of all the employees in the organization, their access controls to various organizational resources. Identity vault is very regularly updated to keep track any changes in the digital identities as well their access controls.
Provisioning / De-provisioning Automation :
Provisioning is the process of providing additional access controls in the organization. De-provisioning is the process of removing or disabling an access control for the resource. Both the processes are automated using the attributes or properties of an identity. For example, you may decide on a few access controls based on an employee’s designation attribute as an ‘IT-Manager’.
However, automation of provisioning and de-provisioning solely based on the identity’s attributes becomes highly complex. For easier management, identity management solutions use RBAC ( Role based access control ). As part of RBAC, virtual entities called roles are created, membership in which can lead to access to various resources. Now, the identity attributes are used to assign the memberships in these roles, thus reducing the complexity.
Process implementations :
Every organization has its own way of doing things. Hence it has its own processes that are internally followed to achieve. Similarly, there are processes that are related to the access controls. We digitally define such processes so that they could be automated . As a subpart of the processes, multiple series and parallel approvals can take place.
Certification :
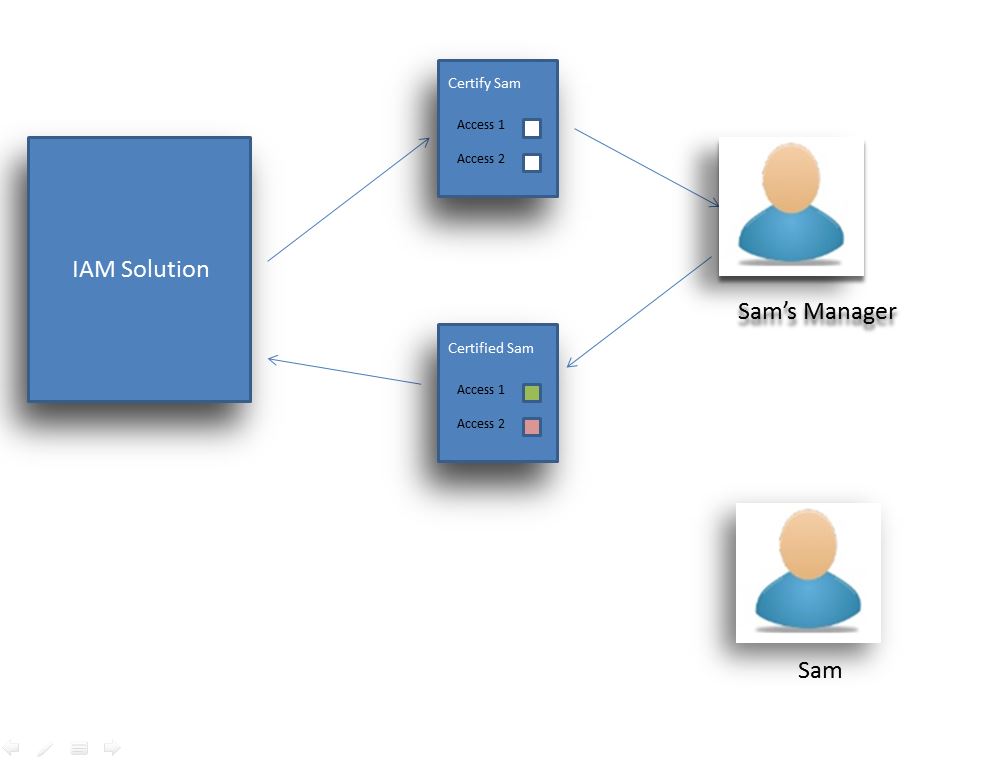
Certification is a mechanism through which periodic monitoring of access controls take place. Access controls of various identities are forwarded to reporting identities where reporting identities can review the access.
Data Archival strategies :
Even with the best of the practices, there will be a need for archiving the data. Identity management solutions also aim to archiving the past data that will not be useful in running the current state of solution.
Reporting :
While all the above mechanisms give a robust and secure system, it would be a lot convenient to have various reports based on the data present with the identity management solutions. For example, SOX reports could be pulled out of the identity management solution very easily based on the access control data available with the solution. Also the reports would be helpful in making various business decisions internally.


 Identity management is the domain which would help the organizations solve most of the problems related to access control that could be solved by proper authentication, authorization and accountability.
Identity management is the domain which would help the organizations solve most of the problems related to access control that could be solved by proper authentication, authorization and accountability. To monitor the JML process , identity management solutions follow various mechanisms through which CIA is actually achieved. The following are the mechanisms that are followed :
To monitor the JML process , identity management solutions follow various mechanisms through which CIA is actually achieved. The following are the mechanisms that are followed :


