Issue Description:
As part of Active Directory Application Configuration in IdentityIQ 7.2, “Test Connection” failing with below error message.

In IdentityIQ 7.2, the Active Directory connector supports multiple Active Directory (AD) forests through one application definition.
While defining the Active Directory application through the IdentityIQ user interface in version 7.2, we do not have the option to mention the server details in Domain configuration settings.
Even though we do not specify any server details, the default configuration tries to connect to “localhost“, similar to the default port configuration which is “389“.
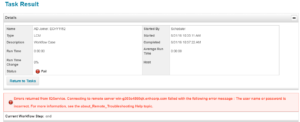
We see the below error message when we click on the “Test Connection”
2018-09-04 05:05:12,551 ERROR http-nio-8080-exec-6 sailpoint.web.ApplicationObjectBean:2701 – Connector failed.sailpoint.connector.ConnectorException: Failed to connect to – dc=enhcorp,dc=com : Failed to connect to server:ldap
dc=enhcorp,dc=com localhost:389
Resolution:
Modify the Application xml file to include the DC servers details.
Below is the example modification.
From
<entry key=”domainSettings”>
<value>
<List>
<Map>
<entry key=”authorizationType” value=”simple”/>
<entry key=”domainDN” value=”DC=enhcorp,DC=com”/>
<entry key=”password” value=”1:iIopEeOL5KrLoSjYKvh/Ww==”/>
<entry key=”port” value=”389″/>
<entry key=”servers”/>
<entry key=”useSSL”>
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key=”user” value=”ENHCORP\Administrator”/>
</Map>
</List>
</value>
</entry>
To
<entry key=”domainSettings”>
<value>
<List>
<Map>
<entry key=”authorizationType” value=”simple”/>
<entry key=”domainDN” value=”DC=enhcorp,DC=com”/>
<entry key=”password” value=”1:iIopEeOL5KrLoSjYKvh/Ww==”/>
<entry key=”port” value=”389″/>
<entry key=”servers”>
<value>
<List>
<String>172.16.153.185</String>
</List>
</value>
<entry key=”useSSL”>
<value>
<Boolean></Boolean>
</value>
</entry>
<entry key=”user” value=”ENHCORP\Administrator”/>
</Map>
</List>
</value>
</entry>