Using JNDI we can access the active directory, but if we want to access the active directory using the secure port we need to get the certificate issued by the active directory certification services.
The certificate helps to authenticate the server over SSL.
SSL authentication is useful when we need to perform the administrative stuff like changing password using JNDI.
Active directory enables us to access the server over SSL using the certificate issued by that server.
To access the active directory using the JNDI we need to get the certificate issued by the active directory and import that into java key tool.
1. Creating and exporting certificate file
We can export the certificate which can accept the SSL authentication in many ways. But in this article we are exporting the certificate using the internet explorer and command prompt.
Note: to export the certificate, server should be installed with active directory certification services. Refer the following link to install the ADCS
i. Exporting the certificate using the internet explorer
- Open in the internet explorer in the windows server and click on internet options
- navigate to content and click on certificate
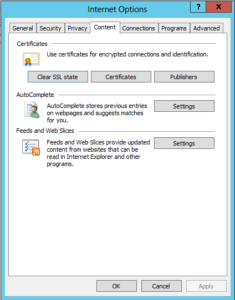
- In the certificates tab navigate to trusted root certificates and click on the certificate with your server name. (in this case server name is ADSERVER)
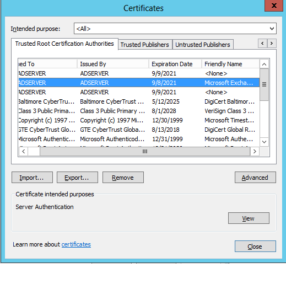
- A new popup will populate with certificate name that you have selected, in that click on details tab and select copy file option.
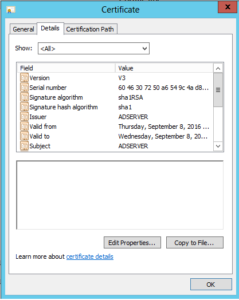
- Then new popup windows will appear, in that click next.
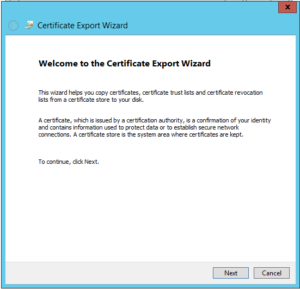
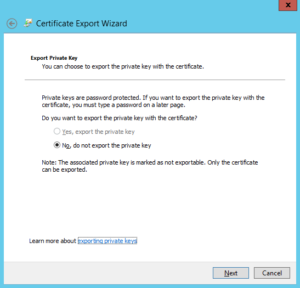
- select the option do not export private key and click next
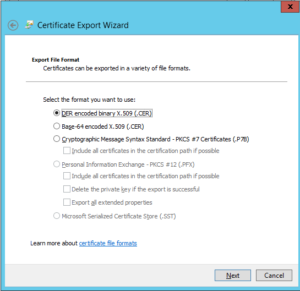
- Select the base 64 encoded and click next.
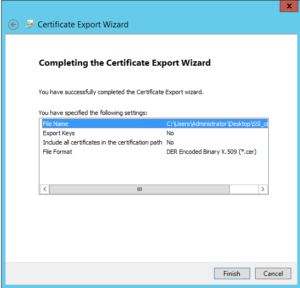
- Provide the path and name to certificate.
- Verify the options and click on finish.
ii. Exporting the certificate using command prompt
- open command prompt in your windows server
- navigate to the folder where you want save certificate
- enter the following command to export the certificate
> certutil -ca.cert sslcert.cer
2. Importing certificate into java keytool
After exporting the sslcert.cer file, copy the file into host machine installed with java.
The following steps explains to import sslcert.cer file into java key tool in various environments
i. Linux
- Open the terminal in the folder which containing the exported file
- execute the following command
# keytool -importcer -keystore JAVA_HOME/jre/lib/security/cacerts -file sslcert.cer
ii. Windows
- Open the command prompt in administrator.
- navigate to the folder containing exported certificate file
- Execute the following command
> keytool -importcer -keystore JAVA_HOME/jre/lib/security/cacerts -file sslcert.cer
